Overview #
I initially created this cheatsheet guide as a personal reference while preparing for the Chef Principles Certification Exam. However i think that more people might benefit and reference this guide before and/or after taking the exam.
Chef has a well designed preparation training and a free exam which you can re-enrol in case that you fail it.
I personally didn’t follow the Chef official exam prep training, but followed the A Cloud Guru learning path instead.
Exam Topics #
- Chef Infra
- Chef InSpec
- Chef Habitat
- Chef Automate
- Chef Compliance
Chef Infra #
Chef Infra is an Automation Platform and is made out of 3 mains components:
- Chef Workstation (how we interact with Chef Infra)
- Chef Server (a central server where the cookbooks are stored and chef clients are pulling the changes from there)
- Chef Infra Client (The nodes that we control the software and infrastructure using Chef Infra)
Cookbooks #
First, we will discuss about Chef Cookbooks.
Chef cookbooks contain recipes and collections of resources, along with the order that these resources should be deployed in our infrastructure. Cookbooks are written with Ruby or Yaml.
Run Lists #
A run list is the list of tasks (recipes and roles) that will be executed in a specific order and configure the node into its end state.
It is specific to a node, but they can be shared among other nodes.
# Example output of a run list
"recipe[COOKBOOK::RECIPE],COOKBOOK::RECIPE,role[NAME]"Policy Files #
Policies are used in order to organise the system’s run list. With Policies, we can choose what gets put into the node.
The Policyfile.lock.json file is generated and uploaded to the Chef Infra Server.
Cookbook Dependencies #
Cookbook dependencies are specified in the metadata.rb file. metadata.rb file is used by the Chef Client and the Chef Server when deploying, and it gets compiles when the cookbook is uploaded to the Chef Server.
How to use Chef Infra? #
- Create a new cookbook with at least one recipe in it
- Upload the Cookbook to the Chef Infra Server
- Add the Cookbook to the run list for the Chef Infra Client
- Run the chef-client command on the client to pull the information from the Chef Server.
Basic Chef Components Hierarchy #
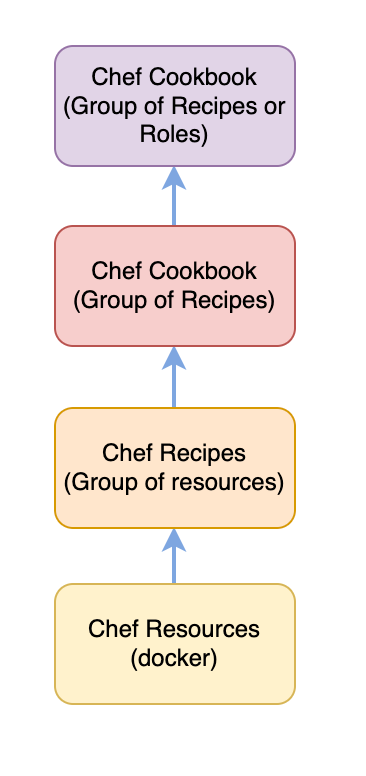
Test Kitchen #
Test Kitchen is installed with Chef Workstation. It allows us to test cookbooks and recipes locally.
Kitchen creates a testing environment (vagrant or docker for example) and tests our Cookbooks inside the linux distribution, running inside docker, that we specify.
Some of the important files that we need to modify when running Kitchen tests:
- kitchen.yml
In kitchen.yml we can specify:
- driver: the environment that the test will run in. Can be vagrant or docker
- verifier_name: The application used for tests. We will use InSpec
- platforms: the operating system and the distribution that we want our Cookbook to be tested
In order to run Kitchen tests with Docker, we need to install a gem (Ruby package) before running the tests.
A typical kitchen test workflow example:
# List all gems installed
chef gem list
# Install kitchen-docker
chef gem install kitchen-docker
### make sure you have a cookbook created with some recipes in it
# Modify the kitche.yml inside you cookbook
vi cookbooks/<cookbook_name>/kitchen.yml
### Specify the
driver:
name: docker
### instead of "vagrant"
### If you added your non-root user in the docker group, you can specify the
driver:
use_sudo: false
### In the platforms section, i will specify a lightweight centos version instead of ubuntu
platforms:
- name: centos
# Kitchen commands
kitchen list
kitchen create
kitchen login # will login to the container
kitchen destroyUsing Knife #
With knife commands. we can manage:
- nodes
- cookbooks & recipes
- data bags, roles, environments
- resources
- bootstrapping
- searching data
The file related to your Knife Profile is the: config.rb file.
Knife quick reference:
https://github.com/chef-boneyard/quick-reference

To understand better how it all tights together, here is a Chef Infra Components from the official chef documentation.
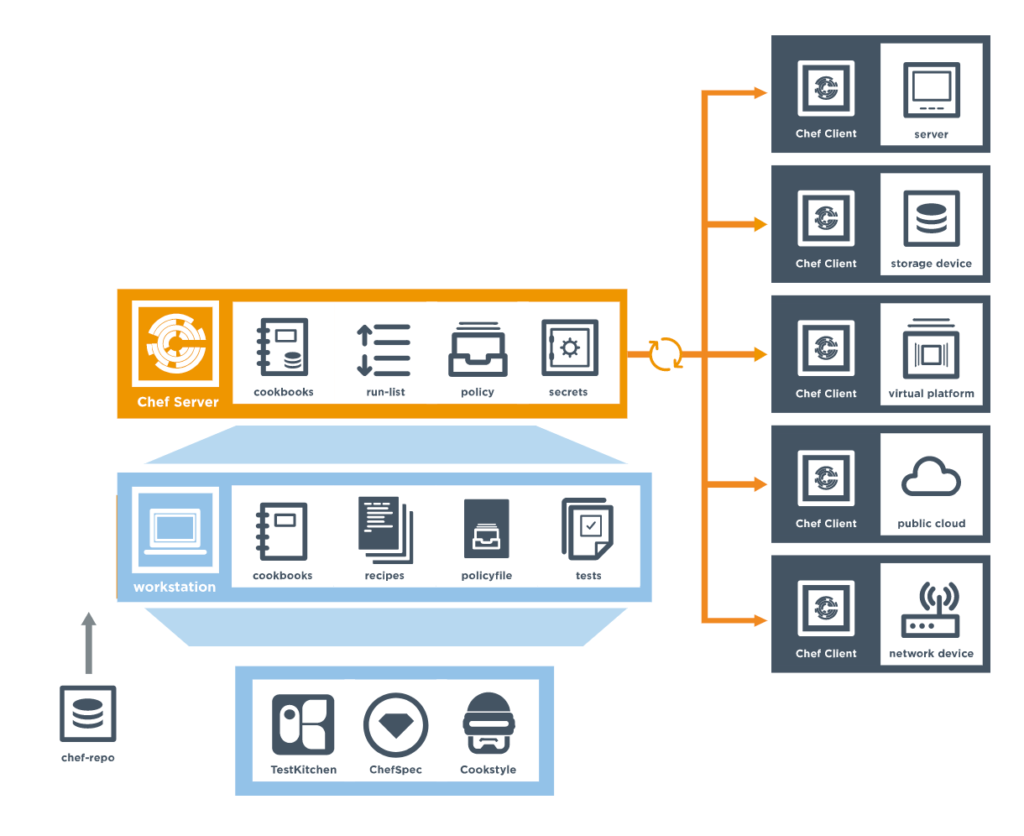
Chef InSpec #
Chef InSpec is a testing framework used by Chef products. We can test application and infrastructure with it.
Add a test to our cookbook #
# Open the following files inside your cookbook directory
vi test/integration/default/default_test.rb
# Here you can add the test. In this example we will test for the httpd package installed scenarion. Assume that there is a package called "name" insatlled in the machine. The test would be
describe package('name') do
it { should be_installed }
end
# Run the command:
kitchen verifyMore test resources can be found: https://docs.chef.io/inspec/resources/
Important InSpec aspects: #
- Matchers: https://docs.chef.io/inspec/matchers/
InSpec Profiles #
Profiles Documentation: https://docs.chef.io/inspec/profiles/
# Head over the chef directory and create a new profile
inspec init profile inspec-test-profile
# Open and write a test
vi inspec-test-profile/inspec.yml
# Run the test profile
inspec exec inspec-test-profileMore inspec test commands can be found in the Useful Commands section.
Chef Habitat #
Chef Habitat centers application configuration, management, and behaviour around the application itself, not the infrastructure that the app runs on. It provides automation that can programmatically and declaratively build, deploy, and manage your application and services, both stateful and stateless. You can deploy and run your Chef Habitat app on many different infrastructure environments including bare metal, VM, containers, and PaaS.
Habitat Cheat Sheet PDF
Chef Automate #
One of the Chef Automate offerings is a GUI where Chef Infra, Chef Habitat and Chef Compliance can be managed.
In the GUI, we can create Notification based on Chef products monitoring. For example Chef Client failures.
Here is a screenshot of the Chef Automate Settings sections with all the options provided from the GUI.
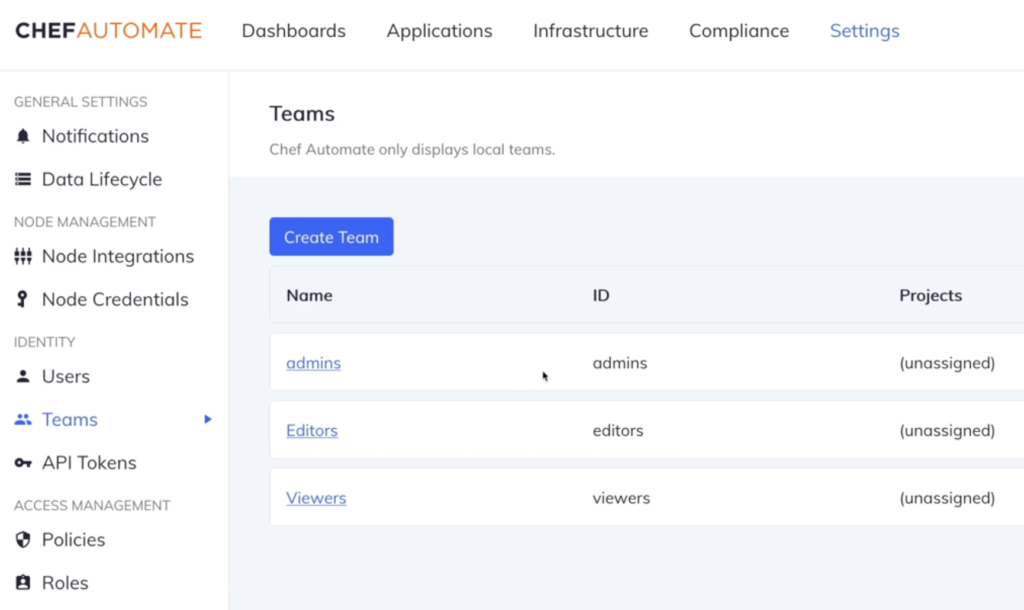
Another Cher Automate offering is a CLI. We can:
- Create backups containing information about all the Chef Products that we are using, which are centralised in the Chef Automate
- Restore backups
- Backup are stored in the /var/opt/chef-automate/backups
We can create a backup with the following command:
chef-automate backup createChef Compliance #
Compliance Profiles tests our systems. With Compliance we can control any issue in the system (form example ignore an issue for a specific time period). Compliance runs with InSpec and we can download Compliance Profiles from external sources like Supermarket. InSpec Compliance Profiles are written in InSpec language.
Here is an example of a Compliance Profile: https://supermarket.chef.io/tools/ssh-baseline, and here are the source code and how to use it against your machine: https://github.com/dev-sec/ssh-baseline.
When a Compliance control is running, and vulnerabilities have been found, we can:
- Fix the found issues from our Chef Infra
- Or, we can use Waivers in order to skip or ignore controls from the Compliance
Here is an example of a Waiver, where the tmp-1.0 grants a waiver until 2023-01-01.
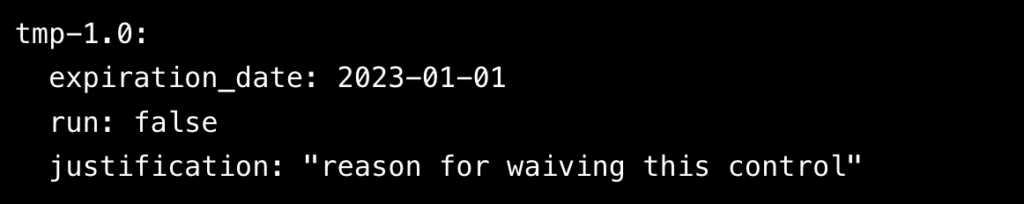
Adding a waiver file and include it when running InSpec test:
inspec exec inspec-test --waiver-file <WEIVER FILE NAME>.yamlChef Compliance can use the following Chef products:
- Chef InSpec
- Chef Infra
- Chef Habitat
With Waiver files you can:
- Enable or disable run option for an InSpec
- You should use justification in the waiver block
- You can set a waiver to run after a specific date
Useful Commands #
Show run-list for a specific node #
knife node show clientExecute ad-hoc commands to one or more target nodes that use Chef Infra Client #
chef-run ssh://my_user@host1:2222 directory /tmp/foo
#will create a directory foo inside the /tmpCreate a new cookbook #
chef generate cookbook install_nginxUpload Cookbook into the Chef Infra Server #
knife cookbook upload install_nginx
# Make sure that you are in the chef base directoryAdd cookbook into specific node’s run list #
knife node run_list add <node_name> <cookbook_name>
# the default.rb recipe will be part of the cookbook's recipe that will be added inot the run listUseful kitchen test commands #
# List tests that have been created
kitchen list
# Create a new test
kitchen create
# Run the tests cases and output the results
kitchen verify
# Login into the environment that the test is running
kitchen login
kitchen destroyUseful InSpec test commands #
# Run local test agains a remote node
inspec exec inspec-test-profile -t ssh://user@hostname
# Run inspec tests agains docker container
inspec exec inspect-test-profile -t docker://<CONTAINER_ID>
# Run inspec tests with profiles available in git repo
inspec exec git@github.com:PATH/PROFILE
# Run inspec tests with profiles available in a webserver
inspec exec https://github.com/dev-sec/linux-baseline
# Run external inspec tests against a remote server
inspec exec https://github.com/dev-sec/linux-baseline -t ssh://hostname.com
###### In case of an ssh error related to the ssh-agent please follow the following steps
eval "$(ssh-agent)"
ssh-add ~/.ssh/id_rsa




